The whole idea behind encrypted folders is to have your own peer on an untrusted device without revealing any of your data. Files get encrypted before transfer, and are not decrypted on the destination.
For example, you may add a copy of a shared folder to a VPS or an available for public use device, without fearing that others will read or use your data. Also, this VPS-hosted peer is going to seed your data 24 hours a day so if your other peers go offline you still have your data accessible.
Please note that having encrypted folders may cause additional memory and CPU use on all devices involved in syncing.
Since Encrypted folders are not meant to be opened or decrypted, a person attempting to open such a folder will see incomprehensible lines of symbols:
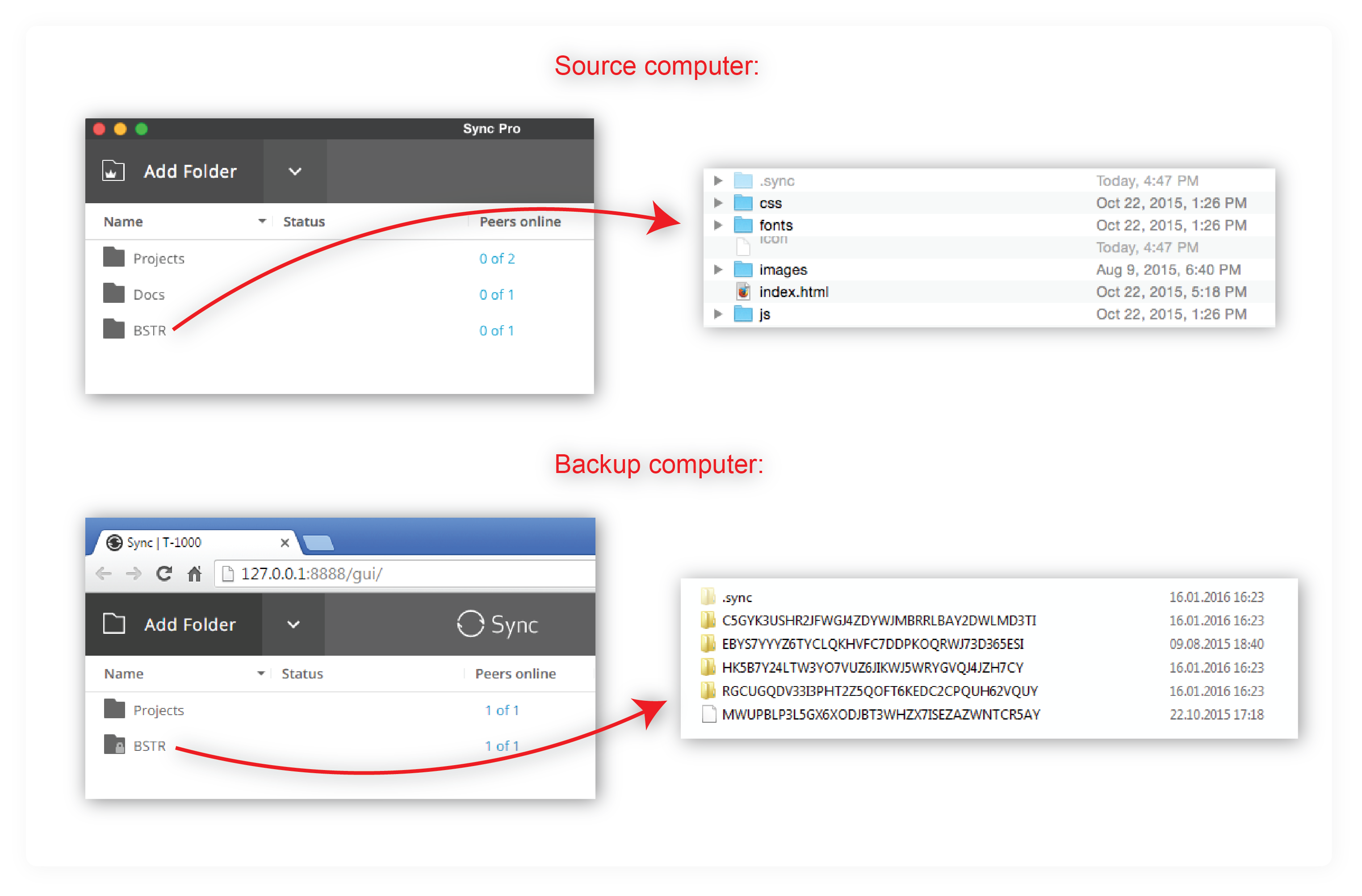
To create an Encrypted folder, click the "+" menu > Encrypted folder > then add a folder from your file system:
Once the folder is created, pass the Encrypted key to another device, where it should be pasted into the Manual connection box (Options > Manual connection):
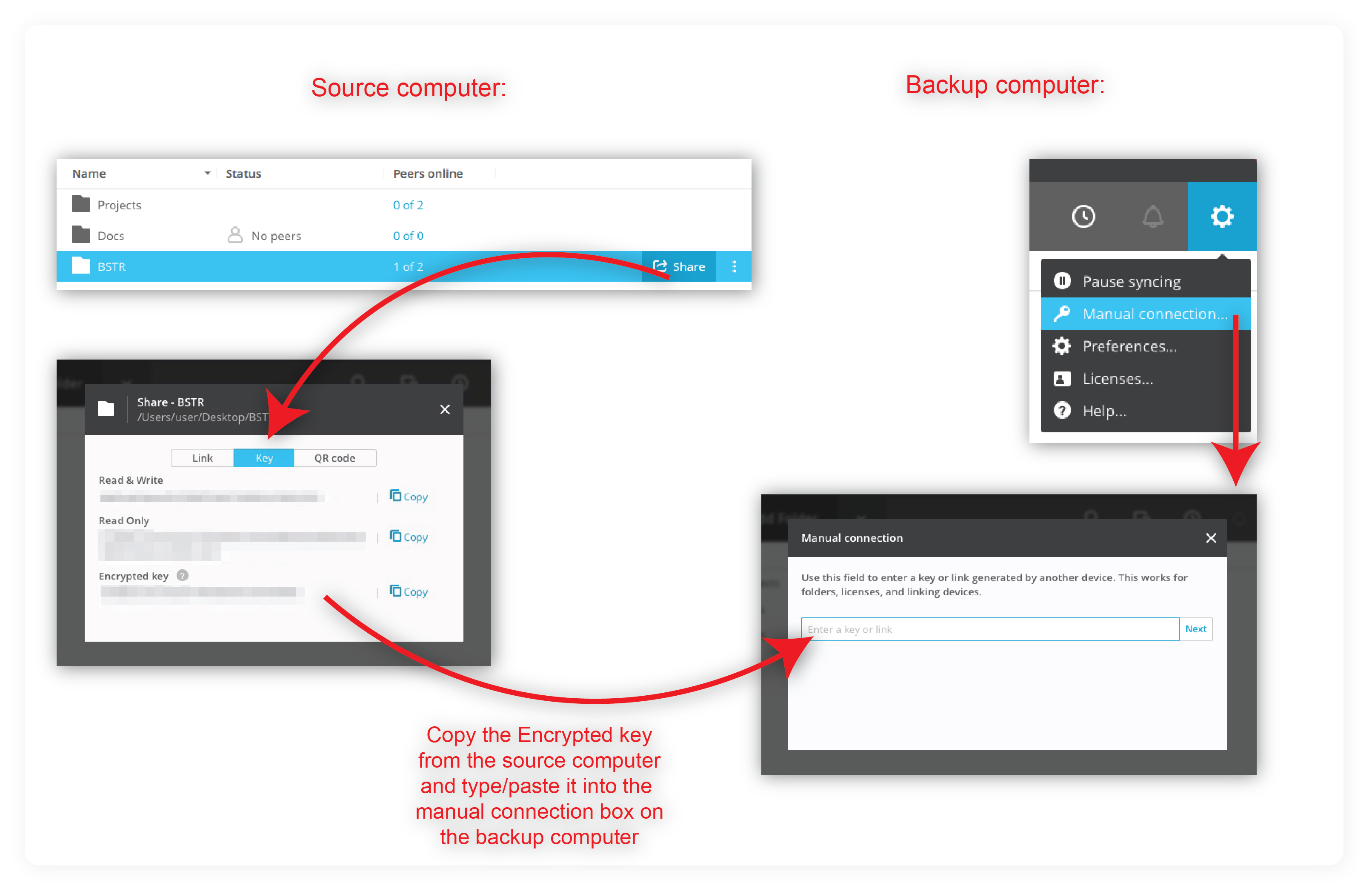
|
To create encrypted folder on devices linked with one identity: - check that linking mode is "Disconnected" for encrypted node; |
You'll be prompted to choose a folder in which the encrypted data from the source computer will be stored. Use your system's file browser to create an encrypted directory. NOTE: do not use a non-empty directory. Files that are already there will not be encrypted, and will be just ignored by Sync. If you pick a directory with files previously encrypted with the same F-key, these files will still be re-synced and moved to Archive. This will lead to extra space taken on the device.
You can share this folder from the backup machine further on, though only in the encrypted format.
RESTORING FILES FROM ENCRYPTED NODE
Encrypted folders on backup machine (the one with F-key only) have Read-Only permissions, "Overwrite any changed files" option is always activated and "Selective Sync" is not available. It means that if you or someone else deletes files on this peer, Sync will download them again from other peers, of course provided they are online and have the files.
Encrypted node does not have decryption mechanism, so it cannot decrypt files.
However, in scenario where peer-source of files fails for a reason, there is a chance to get the files from encrypted backup peer. For that, two conditions must be met:
1) Save RW and RO (D- and E- accordingly) keys to this folder somewhere.
2) Do not remove encrypted folder from Sync on encrypted node, so that the database remains the same as initially created.
In this case, you can use the RW key on the main workstation. It will connect to the encrypted node and download the files from it. The RW key (D- key) can decrypt them.
Another way to decrypt files is to do it locally on the encrypted node in command line interface with command
--decrypt <secret> <db path> <encrypted folder> <output folder>
<secret> is RW key from source peer.
<db path> is the full path to database file. Database name can be learned from the debug sync.log: find string "started periodic scan" and see shareID there. Database file will have these at the end of its name. Else please contact support and submit debug logs to them.FC[858F]: started periodic scan for "C:\my_encrypted_folder"
<encrypted folder> - path to the encrypted folder on the encrypted node.
<output folder> - path to store the decrypted files. This folder must be created before decrypting.
RESTORING FILE FROM ENCRYPTED ARCHIVE
Encrypted node, being a regular Sync peer, also has its Archive, which works the designed way. However in scenario where peer-source of files get an important file deleted, encrypted node is not capable of restoring it from Archive and uploading back for two reasons:
- it has "Overwrite any changed files" enabled by default, and the file has state "deleted" on the source peer. Thus encrypted node follows the state.
- it's a read-only peer, so it won't be able to upload restored files.
To get the deleted file back either restore them from recycle bin, or from Archive on other connected Read-Write peers.